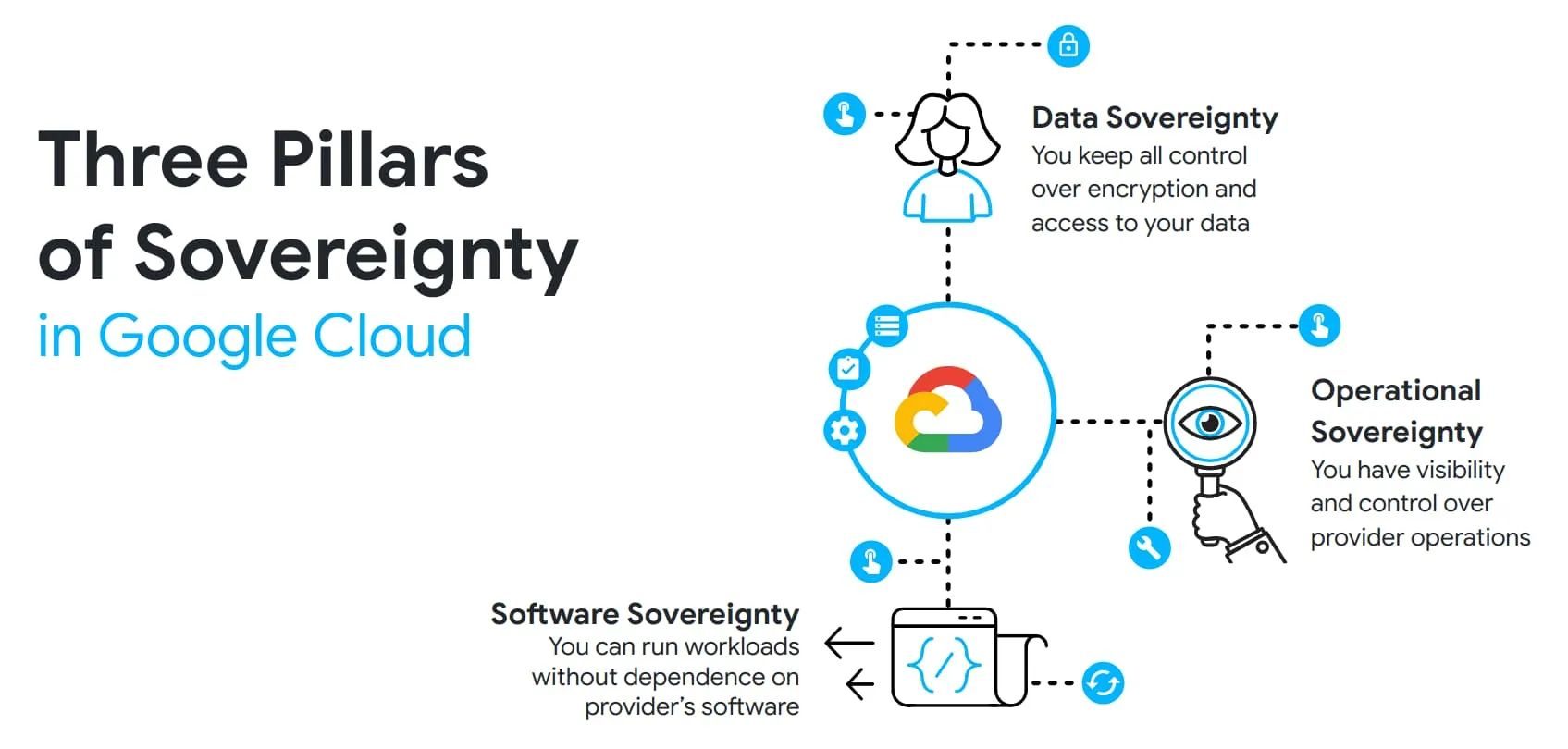
Source: cloud.google.com
For several years we have created GDPR compliant solutions.
Now we’ve perfected it with a Digital Sovereignty compliant architecture.
The architecture is based on an integration between the mail marketing platform, the website and the CRM.
With the new Digital sovereignty compliance we have full control over the location of all data, all documents, all applications, enclosing them all in a fence that can be as rigid as we want and be able to strengthen it in transparency with respect to the operating procedures of the users who they will not notice the changes on the infrastructure.
This infrastructure is even cheaper than solutions that today seemed to be the limit beyond which savings were at the expense of security and business continuity.
Within the enclosure of digital sovereignty it is possible to place personal, departmental documents and personal mail clients. So each user will be able to choose the platforms and methods on which he boasts a higher competence and productivity.
It is also possible to use “data lake” architectures that allow the total sharing of data to all those in possession of adequate credentials.
In practice, the company’s know-how is distributed uniformly both horizontally (increased data availability) and in greater depth (increasingly more specific and more technical details).
In practice, on each employee’s laptop there are “copy” versions downloaded from the data lake or to be uploaded to the data lake because in isolation they cannot be integrated with all the corporate data whose residence and interactions are possible are within the digital enclosure sovereignty.
For example:
- the mail client is in the data lake
- excel sheets and word documents
- the presentations
- the CRM
- the ERP
- The project management
- the Web site
- personal notes (block notes, appointments, etc.)
In the enclosure of digital sovereignty there is software that can be open source (therefore within the servers located in the company), it can be a service managed by a third party that can use the private, hybrid or public cloud.
They are residents, for example:
- all applications used by the customer
- all private areas that are in the file server
- all databases
- all corporate documents
- recording of all communications made on authorized devices.
However, privacy is only one of the aspects that protect the consumer, the tax aspects of each country and the national sovereignty that is subservient to the government’s political strategy.
Without going into the issues relating to data sovereignty and digital sovereignty, thus remaining strictly within the scope of the differences between GDPR & CCPAS, we summarize the most significant differences:
Switzerland, for example, has imposed that personal and business data must not leave the Swiss borders.
The software we are using was developed in Germany under the name of Digital Sovereignty.
Within this concept we therefore find
- the privacy policy
- the cookie policy
- option in/out on email and the use of mobile advertising
- identification of the subject
- the person in charge of personal data
- right to be forgotten (RtbF)
- right to withdraw consent (RtwC)
- right to be an explanation (RtaE)
- the sales and taxes that are highlighted in an invoice for a service dedicated to a resident entity in the country
- the digital invoice
Last Updated on June 5, 2024