Home » Digital Sovereignty
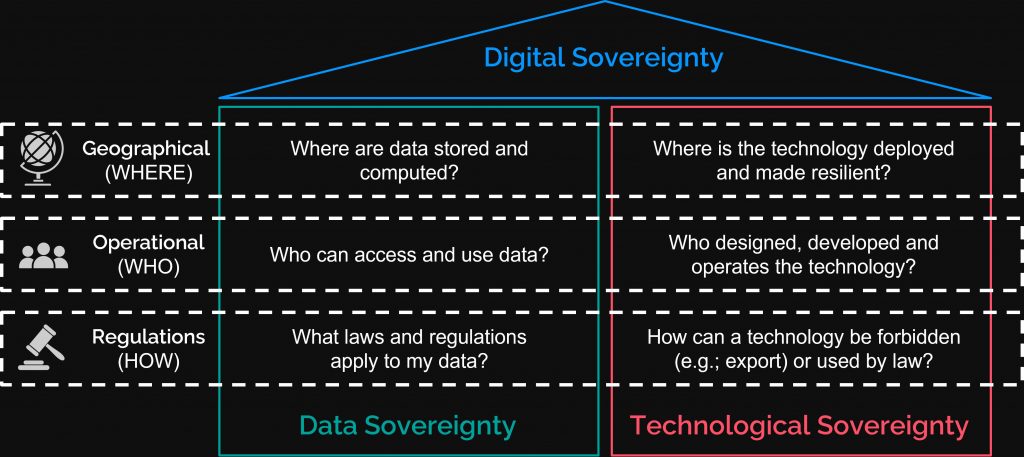
Despite its significance, the exploration of Digital Sovereignty remains in its nascent stages. It intersects various research domains such as geopolitics, technology, and economics, necessitating more robust research endeavors to comprehensively grasp the concept. Originally, Digital Sovereignty emerged as a response to concerns regarding data privacy and ownership, often propelled by political agendas seeking “internal legitimacy” to appease citizens.
Subsequently, it was delineated and analyzed across diverse technological sovereignty realms, encompassing digital, network, data, spectrum, Internet, cybersecurity, computer, and information domains. Recently, the concept of digital sovereignty has garnered increased attention, particularly in two dimensions:
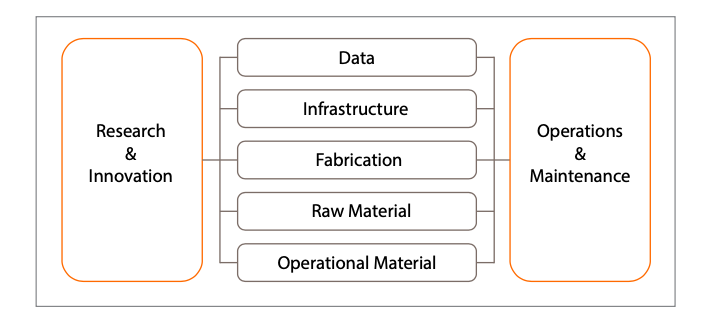
As a response, a comprehensive definition of digital sovereignty has been introduced, encompassing the entire spectrum of a state’s digital assets. This definition encompasses data, infrastructure, fabrication, raw materials, operational resources (both material and human), and research & innovation.
Alternative Definition
The Modern Internet Architecture
Extracted from arxiv.org
An online storage service facilitates file storage and sharing over the Internet. Previously restricted to workplace use, data accessibility has now expanded to anywhere, be it at home or on the go, enabling multiple users to share data. Utilizing an online storage service offers several advantages:
The utilization of online storage services not only enhances user convenience but also diminishes the workload of system administrators. However, in recent years, several issues have surfaced, posing risks to businesses.
For a comprehensive understanding of “Digital Sovereignty” and why governments perceive data and digital technologies as strategic infrastructure see the reference below.
reference: deltalogix.blog
We manage it via plesk.com, which simplifies any system operation
NextCloud:
It can be installed in an on-premises environment such as your own server room or data center. Additionally, it can be deployed on corporate public cloud services such as Amazon AWS and Microsoft Azure. The server OS is compatible with Linux, and installation on an existing virtual environment is also possible.
With support for multiple devices, NextCloud can be accessed not only from a browser but also through dedicated applications that synchronize for each folder, including specialized apps for smartphones and tablets like Android and iOS.
In addition to file sharing among NextCloud users and groups, files can be shared with individuals who do not have accounts, such as business partners. Integration with existing user management systems such as LDAP and Active Directory is possible, as well as support for SAML 2.0 for linking with existing single sign-on systems.
File operation logs are manageable, and since NextCloud is built within your company’s environment, logs can be managed to comply with your company’s rules and regulations.
Support costs are billed based on the number of users, with storage capacity and data usage charges unaffected. Expansion of capacity according to the customer’s needs is straightforward.
On-Premises or Cloud:
Security:
Expertise:
Influence:
Administrations:
Storage Savings Lead to Reduced Purchases
Reducing storage space requirements translates to fewer disk purchases, as the rate of information growth slows down significantly.
All applications, including local ones like Office, are installed within the NextCloud environment, eliminating duplications entirely.
Even email storage growth will decelerate as the IT culture permeates both internal and external users of the company.
Load Balancing for Stable Performance
Deploying multiple instances of NextCloud “federated” with each other ensures stable performance.
Redundancy Ensures Business Continuity at No Extra Cost
For 24/7 business continuity with minimal costs, redundancy can be guaranteed by creating federated NextCloud nodes.
Hybrid Architecture for Cost Reduction
Various architectures based on NextCloud technology are feasible, such as:
It’s no coincidence that 70% of companies are transitioning to infrastructures based on private clouds, fully compliant with GDPR, gradually phasing out their on-premises infrastructure.
Reduced Need for Standby Devices
Immediate recovery of faulty computers is possible since no critical data resides on each user’s desktop, laptop, or smartphone. Resources remain accessible via password from any Internet-connected device.
Reduced Device Obsolescence
Budgets allocated to prevent computer fleet obsolescence decrease as low-performance computers no longer impact user performance, with processing now handled on the server rather than locally.
Lower Bandwidth Requirements
Bandwidth usage decreases due to reduced data volume movement and significantly fewer email exchanges, which no longer include attachments. Response quality depends on bandwidth and the server quality where NextCloud resides, transmitting only changes instead of heavy data.
ROI Achieved Within a Year
Statistically, companies adopting digital sovereignty via NextCloud technology see returns on their investment within 12 months. Costs continue to decline in subsequent years as NextCloud becomes more entrenched in corporate culture.
Administrators can track who modified a file within the system.
View and edit documents directly within your NextCloud environment. Users have the ability to insert and respond to comments, as well as invite others to collaborate, even if they don’t have a NextCloud account, through anonymous editing of files with a shared public link folder.
NextCloud supports a wide array of document formats, including DOC, DOCX, PPT, PPTX, XLS, XLSX, ODF, Import/View, Visio, Publisher, and many others.
Simultaneous editing of the same file eliminates the need to repeatedly transfer files between multiple users, preventing confusion and potential loss of changes and their history.
Without this technology, the process could be tedious and even risky. In a typical scenario, one person makes corrections and sends the file to another, who then makes further edits, creating a cycle of endless back-and-forth exchanges.
With NextCloud, I can share access with another internal NextCloud user or with a non-NextCloud user, such as when reviewing a contract with a client.
For added security, I can:
There are other available options that can prove highly beneficial in various situations.
Ensure the privacy and security of your online conversations, meetings, and video conferencing with NextCloud Talk.
Unique Protection
NextCloud Talk provides on-premises, private audio/video conferencing and text chat capabilities via browser and mobile interfaces. It also offers integrated screen sharing and SIP integration (Session Initiation Protocol) for added functionality.
Complete Control
Maintain full compliance with business and legal requirements by keeping your data on servers you own at all times. With NextCloud Talk, nothing leaks, not even metadata.
Compliance
Self-hosting communication simplifies compliance with national and international privacy and security regulations. By leveraging existing, vetted infrastructure, your current compliance and security processes seamlessly apply to NextCloud Talk.
Reference:
nextcloud.com
youtube.com
youtube.com
There is a wide array of apps available, including email, calendar, social networking, and more.
We have the capability to develop custom modules tailored to your specific requirements.
Administrators have the ability to assign usage to carefully defined users with various levels of credentials.
Most of the apps are free, while others are offered on a freemium basis.
Reference: apps.nextcloud.com
The NextCloud Desktop Sync Client allows you to connect seamlessly to your NextCloud Server. You can create folders in your home directory and keep their contents synchronized with your NextCloud server. Simply drop a file into the directory, and the NextCloud desktop client takes care of the rest. Any changes made to files on one computer will automatically propagate to others using these desktop sync clients, ensuring you always have your latest files wherever you go.
Desktop Sharing
The NextCloud desktop sync client integrates smoothly with your file manager, whether it’s Finder on macOS or Explorer on Windows. Linux users may need to install an additional package depending on their chosen file manager. Options include nautilus-NextCloud (Ubuntu/Debian), dolphin-NextCloud (Kubuntu), nemo-NextCloud, and caja-NextCloud. With this integration, you can create share links and collaborate with internal NextCloud users just as you would through your NextCloud Web interface.
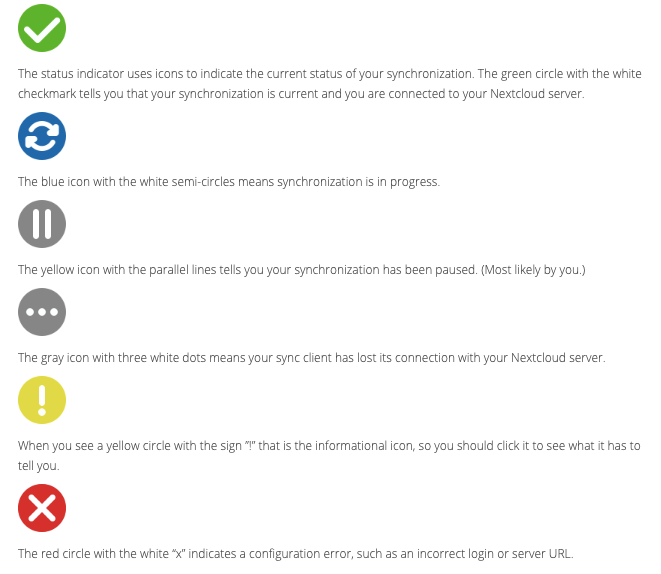
Using the Synchronization Client
The NextCloud Desktop Client operates quietly in the background, appearing as an icon in the system tray (Windows, KDE), menu bar (Mac OS X), or notification area (Linux).
Reference:
docs.nextcloud.com
docs.nextcloud.com
The desktop can remain permanently idle or disabled if necessary. In the event of a breakdown, the desktop can be replaced without causing any inconvenience to the user. Users can seamlessly work with both the desktop and the smartphone app simultaneously.
This architecture significantly mitigates technological obsolescence since obsolete desktops can be recycled without any disadvantage compared to users with the latest desktops.
Multiple NextCloud instances can be synchronized, ensuring efficiency and security even when syncing with customers’ clients.
Security by Design in NextCloud Hub
NextCloud Hub is designed with security in mind, allowing you to host your data locally or in the trusted cloud. Flexible sharing options help control access not only to the files in your storage but also to other items such as Deck boards, Collectives, and more.
Enterprise-class authentication security in Hub provides features like 2FA, SSO, SAML 2.0, support for LDAP/Active Directory, and reliable backup options, including peer-to-peer backup for private users with the NextCloud Backup app.
Utilize Temporary Links
Temporary links are a powerful tool that enhances file security with minimal effort. They limit access time for the target user when revoking access is not an option, reducing the opportunity window for unauthorized access. This feature is especially valuable when sharing files temporarily for specific purposes or events.
Be mindful of the link’s expiration date and select a secure and reputable file-sharing service. Additional security measures such as encryption in transit and at rest should also be employed to ensure comprehensive protection of shared files.
External Link Sharing in NextCloud
In NextCloud, you can securely share file and folder links with optional expiration dates. If your link circulates, rest assured it won’t be active for long. Forgotten shares are automatically rendered inactive, eliminating the need for manual access revocation.
Restrict File Reuse
Prevent inappropriate reuse of shared content by implementing additional measures.
Apply Watermarks
Watermarks protect document content by embedding essential information about the author, such as name and creation date. In NextCloud Hub, you can use watermarks and hide the download option from other users. Additional permission levels can be applied to forbid certain actions like editing and deleting. External link sharing is centrally managed in the link settings and can be revoked at any time.
Restrict Downloads
Some sharing options include download restrictions, allowing users to access files online but preventing them from downloading, redistributing, or uploading the content elsewhere.
Password Protection
NextCloud Office enables you to protect links with passwords, ensuring only authorized users can access shared files even if the link becomes public. This feature also safeguards individual files when sharing folders publicly, offering greater convenience compared to file encryption.
Encrypted File Sharing in NextCloud
The NextCloud desktop client offers client-side end-to-end encryption as a folder-level feature, enhancing the security of highly sensitive data, even in the event of a server breach.
Secure File Sharing with NextCloud Hub
NextCloud Hub prioritizes privacy, making it one of the safest collaboration platforms available. Every app within the ecosystem, including Mail, Talk, Calendar, Notes, and Files, is designed with privacy in mind, working together seamlessly to deliver top-notch collaboration for individuals and enterprises.
Moreover, NextCloud Hub is free and unlimited for both private users and companies. Opt for the Enterprise version to receive 24/7 dedicated support and a stable performance guarantee for mission-critical deployments.
File synchronization and sharing with NextCloud are available on mobile platforms and desktop environments, ensuring a high level of privacy and convenience.
Reference: nextcloud.com
Today, the exchange of emails is increasingly limited and minimized due to its potential for trouble and as an unmanageable security vulnerability. Mail providers implement stringent measures to prevent spam and avoid IP bans.
As a result, it’s advisable to steer clear of emails with content, especially attachments!
Instead, consider utilizing transactional emails, such as notifications. NextCloud employs this method for file sharing and other activities where activating this technique is appropriate.
NextCloud supports Single Sign-On (SSO) and offers native SAML 2.0 (and Shibboleth) authentication within its web interface. The native SAML integration eliminates the need for external software such as Apache modules. Native SAML is compatible with all web servers and supports group memberships, flexible session management, and application-specific passwords.
Single Login Point
The Global Site Selector serves as the primary login instance for all global users. It redirects logins to the node closest to the user’s physical location, ensuring subsequent calls are executed within that node.
Reference: nextcloud.com
Several features are already accessible: Image object recognition, Video action recognition, Audio music genre recognition, Suspicious login detection, and Speech-to-Text capabilities.
Ethical AI Rating
Up until Hub 3, we’ve successfully offered features without relying on proprietary blobs or third-party services. However, while there’s a thriving community developing ethical, safe, and privacy-respecting technologies, users may desire other relevant technologies. We aim to provide users with these cutting-edge technologies while maintaining transparency. While ChatGPT might suffice for some use cases, for more private, professional, or sensitive data, having a local, on-premises, open solution is crucial. To distinguish between these, we’ve developed an Ethical AI Rating.
Reference:
docs. docs.nextcloud.com
Some EU governments have embraced NextCloud as part of their digital sovereignty initiatives. European governments are increasingly prioritizing digital independence by moving away from cloud solutions provided by large, centralized, foreign companies. With the introduction of GDPR and legal challenges to the US Cloud Act, several European government entities, including the French Ministry of Interior, the Dutch Ministry of Education, and Swedish federal government agencies, have followed the lead of the German federal government in adopting a European-designed, private cloud solution.
Over the past year, the French Ministry of Interior has assessed the feasibility of establishing an internal cloud infrastructure and is now preparing to implement a production-ready NextCloud solution for its users. This solution is designed to accommodate the ministry’s 300,000 employees and will provide them with easy, secure file exchange capabilities accessible via mobile, desktop, and web platforms, along with real-time collaborative office document editing.
According to the Swedish National Procurement Services, Sweden recognizes the importance of maintaining control over its information for reasons of national security and sovereignty. The potential implications of not having access to critical information during international crises or conflicts underscore the necessity of ensuring that information handled by service providers remains within national jurisdiction.
Reference: nextcloud.com
In the summer of 2020, the European Court of Justice issued a highly anticipated and far-reaching ruling. The court found US law to be incompatible with EU privacy regulations due to US government agencies accessing data of EU citizens held or managed by US companies. This contravenes the Charter of Fundamental Rights of the European Union and the GDPR.
Reference:
nextcloud.com
NextCloud offers users a modern, user-friendly, and productivity-focused platform that facilitates efficient online and mobile collaboration and communication. ITZBund now implements an on-premises open-source solution from a German provider to maintain control over its own data.
ITZBund serves as the central IT service provider for the German federal government, managing IT services for over one million administrative and industrial users. Formed from the merger of the Federal Agency for Information Technology (a division of the Federal Ministry of the Interior), the Federal Agency for IT Services (a division of the Federal Ministry of Transport and Digital Infrastructure), and the Center for Information Processing and Information Technology (a division of the Federal Ministry of Finance), ITZBund employs approximately 2,700 individuals, predominantly comprising IT specialists, engineers, and network and security professionals.
Reference: nextcloud.com
Ensuring Data Security in a Globally Distributed Organization
The Konrad Adenauer Foundation (KAS) stands as one of Germany’s most influential political think tanks. With over 1,000 employees spread across 16 offices in Germany and 107 abroad, the organization deals with politically sensitive data in regions where individual freedoms are frequently challenged. To uphold the highest standards of security and privacy, KAS has selected NextCloud as its self-hosted, private collaboration platform.
NextCloud has revolutionized remote work, providing a secure environment for employees to collaborate regardless of location.
Source: nextcloud.com
Stadtsparkasse Munich
Stadtsparkasse Munich streamlines customer data exchange through NextCloud by HKN
Cloud-Centric, Cloud-Focused
For some time now, Stadtsparkasse München has operated an on-premises NextCloud server to securely exchange confidential data with customers. In 2020, the bank made a strategic decision to transition all internally managed systems to the data centers of competent, regional partners. With a Gold Partnership with NextCloud, HKN emerged as the ideal partner to host their NextCloud services.
NextCloud offers a unique on-premises solution tailored for financial services companies.
Reference: nextcloud.com
Your Dashboard serves as the launching pad for your day. Picture yourself with your favorite cup of coffee or tea in hand, ready to dive into your tasks.
Who reached out to you? Is there a crucial email awaiting your response? With the NextCloud Dashboard, you gain a swift overview of all activities within your NextCloud ecosystem, empowering you to kickstart your day with productivity in mind. Easily resume where you left off on a project using the Deck widget or stay ahead of upcoming tasks.
The array of widgets available ensures versatility, and with some practice, you can even craft your own!
Reference:
apps.nextcloud.com
nextcloud.com
Just the email app client.
For a NextCloud email server you could run mailcow.email or mailinabox.email or mailu.io/2.0 in addition to your NextCloud instance. Or setup postfix.org etc. There are endless threads about this on this forum’s search or from google.
Using the Mail app
The Mail app comes installed with NextCloud Hub by default, but can be disabled. Please ask your Administrator for it.
Quick description
Authentication and Group Management
The Lightweight Directory Access Protocol (LDAP) servers, such as Active Directory (AD) or OpenLDAP, are commonly utilized in large organizations to provision, authorize, and manage users. Centralizing user accounts simplifies user management and facilitates IT oversight of access rights. NextCloud supports user authentication via the LDAP protocol and manages properties like group membership, user details, and more across one or multiple LDAP server connections, in addition to local accounts.
Technical Specifications On the NextCloud Side:
Technical Specifications On the LDAP Side:
Reference:
docs.nextcloud.com
docs.nextcloud.com
“We chose NextCloud primarily for its ability to authenticate users against our LDAP directory, coupled with its open-source approach. This not only grants us control over our data but also over the entire software infrastructure, allowing us to customize which aspects of the NextCloud system we enable or disable.”
Reference: docs.nextcloud.com
Consistent Backup and Restore of Complex Application Data
Now, you can configure Backup to routinely store compressed, encrypted backups of your data on their NextCloud server! In case of any mishaps, you can effortlessly restore your NextCloud or even retrieve individual files and folders. Moreover, it may be advantageous to reciprocate by creating an account for them on your server to safeguard their backups!
What sets NextCloud Backup apart from other backup solutions? Its simplicity! If you’re already comfortable with a particular backup technology, feel free to stick with it. NextCloud Backup is designed for users who have encountered difficulties and time constraints in setting up alternative backup solutions.
ref.
docs.nextcloud.com
help.nextcloud.com
docs.nextcloud.com
nextcloud.com
Ensure compliance with ISO 9001 and ISO 27001 standards by avoiding the physical transfer of files between users.
NextCloud solutions excel in empowering their business customers with the ability to “know where data is, who has access, and ensure that even metadata remains secure.” It’s a security-first approach that permeates their design, development, and product positioning, and it’s by design, not happenstance.
However, in today’s world, claiming to put “security first” is often mere marketing rhetoric. With NextCloud, it’s a foundational element of their entire business strategy, enabling them to adopt an assertive stance on security. This commitment also empowers their small security team to achieve an impressive average response time of less than 1 hour on their HackerOne Bounty program.
NextCloud has elevated security from a mere cost center to an integral aspect of their business ethos and messaging.
Presently, NextCloud offers several security measures, including double authentication factor, data access control, and server monitoring. Indeed, NextCloud stands out as a more secure alternative to other mainstream tools, particularly because it allows hosting on personal servers and in on-premises mode.
Multilevel Authentication
NextCloud incorporates Universal 2nd Factor (U2F) and Time-based One-Time Password (TOTP) second-factor apps to enhance the security of user login procedures.
References:
nextcloud.com
nextcloud.com
Keepass
Keepass is an open-source password manager with seamless integration into NextCloud through the Keeweb app.
Enpass
Enpass is an offline password manager that allows users to securely store and synchronize their data using their preferred cloud accounts, ensuring heightened security with 2FA enabled. It offers a comprehensive set of features comparable to other password managers in the market. The desktop version (compatible with Windows, Mac, and Linux) boasts a user-friendly interface. While free, registration is required for full access. The iOS and Android apps feature excellent user interfaces but require payment for use beyond managing 25 passwords.
Passwords
Passwords is an advanced NextCloud application designed for securely managing and storing passwords within your personal cloud.
The app’s intuitive and contemporary web interface facilitates easy password updates and additions from any location. Additionally, built-in security checks help maintain the safety and currency of your online accounts. You can also share passwords with other NextCloud users, organize them into folders, and recover deleted passwords.
Passman
Passman stands as the longest-serving NextCloud password manager, offering a rich array of features, including the ability to share passwords seamlessly.
Reference:
nextcloud.com
Security Properties
The following security properties must be met:
Encrypted folders must adhere to the following encryption scheme criteria:
Confidentiality
Only legitimate recipients should access encrypted documents.
Integrity
Even with writable access to the ciphertext, tampering with data should be impossible. If an encrypted file referenced in the metadata is deleted from the file system, a warning should alert the user.
Authenticity
The authenticity of files must be ensured.
Reference:
nextcloud.com
NextCloud Enterprise supports standards such as GDPR, CCPA, HIPAA, FERPA, COPPA, various ISO certifications, and many others.
Its compliance features encompass tracking terms of service reviews, handling data export/deletion requests, providing imprint and privacy links, and auditing capabilities.
Reference:
nextcloud.com
Forward
Digital Sovereignty must be at the forefront of the agenda for every modern nation. It is becoming an increasingly urgent priority to shape the present and future of nations and has become a pivotal issue that can either make or break a country. Digital sovereignty is imperative for maintaining a state’s independence and safeguarding national security in the face of escalating threats to digital assets.
These threats emanate from both allied nations (e.g., USA, Germany, Canada, and Brazil) and non-allied nations (e.g., USA, Russia, China, and Iran).
Protecting digital assets from these threats, whether they are rational or malicious, is crucial for modern countries due to the unprecedented integration of digital technology into our daily lives.
The absence of digital sovereignty can jeopardize automated and smart digital systems such as water systems, food supply chains, smart power grids, telecommunications, the Internet of Things, economy, health services, governance, security, and defense. Consequently, if these digital assets are compromised, national security will be compromised, and human lives will be endangered.
Achieving digital sovereignty poses significant challenges. We highlight two main strategies proposed in both literature and practice:
Nash Equilibrium Sovereignty is inspired by the Nash Equilibrium strategy in Game Theory, representing a hybrid cooperative and non-cooperative approach, in contrast to the cooperative bargaining strategy. Nash Equilibrium enables two players to reach a stable outcome without necessarily intending to cooperate directly.
Classical bargaining relies on negotiations aimed at maximizing the decision utility, which represents the payoffs expected in the future, as proposed in the Neumann–Morgenstern (VNM) utility theorem in 1953. Formally, a two-person bargaining problem consists of a pair (F, d), where F denotes the set of feasible agreements and d represents the disagreement point (payoffs) if the negotiation fails. The solution lies in finding a function f that takes a bargaining problem (F, d) as input and yields a feasible agreement as an outcome, i.e., f (F, d) ∈ F. The process of finding the solution f may involve different criteria, such as maximizing the product of gains (Nash Product) or equalizing the gains, among others.
This excerpt is taken from “Digital Sovereignty Strategies for Every Nation” available on arxiv.org
Comparing Self-Sovereign Identity Solutions for Blockchain-Based Land Registry Systems
Introduction
The land registry stands as a crucial economic foundation in nation-building for any country. Utilizing blockchain technology can bolster security and transparency within land registries by recording pertinent land details on the blockchain. Furthermore, blockchain expedites property identification and augments trust and precision in transactions by enabling digital oversight by stakeholders.
The proposal builds upon mature concepts ready for implementation.
The Concept of Self-Sovereign Identity
Self-sovereign identity (SSI) represents a groundbreaking approach to identity management. Initially, digital identities were under the control of centralized organizations, while individuals stored their identity information in a decentralized manner using physical wallets. SSI aims to bridge online identity systems with the real world, empowering users with control over their identities. In practice, after a child’s birth, government authorities issue identity credentials such as birth certificates and identification numbers. These credentials serve individuals in various scenarios throughout their lives.
Blockchain Technology and Self-Sovereign Identity
Self-sovereign identity systems leverage blockchain technology. Blockchain, an advancing technology, utilizes cryptocurrency to offer a decentralized, openly shared ledger applicable for electronic voting and land registration. Cryptocurrency represents just one of blockchain’s many potential applications. Blockchain’s technical attributes position it well to drive significant changes in digital identity management.
Self-Sovereign Identity and Land Registry
Self-sovereign identity (SSI) plays a pivotal role in land registries by furnishing individuals with identities for communication with land management services. Currently, approximately one billion people worldwide lack proper identification records. SSI presents an opportunity to establish increasingly secure and trustworthy identities without reliance solely on government-approved documents. By aggregating certificates from reputable third parties like land registries and financial institutions, SSI enables individuals to substantiate their property claims even in the absence of legal documentation. SSI credentials offer robust authentication and should extend beyond digital replicas of traditional paper documents. SSI can serve as a framework for transforming data into credible credentials, earning the trust of administrative agencies. For instance, individuals can utilize their verified location history from mobile providers in conjunction with land registry certificates to validate ownership claims.
References:
Exploring the concept of data sovereignty raises intriguing questions. Firstly, data contains information pertaining to specific populations within particular territories. This data may be transferred, stored in different jurisdictions, or generate metadata associated with populations whose ownership is ambiguous. Applying principles of sovereignty to data also necessitates an examination of a state’s capabilities and priorities in meeting international obligations regarding data management. Consequently, among a state’s enumerated responsibilities, as outlined in the 11 norms, is the protection of data and the promotion of privacy practices in accordance with human rights.
References:
Introduction
Companies typically utilize an average of 17 distinct applications, each tapping into customer data alone, as reported by deloittedigital.com. Ensuring compliance across these applications, along with any employee data technology, presents a multifaceted challenge. It’s worth noting that 92% (see oliverwyman.com) of the Western world’s data is housed in the US, where regulatory frameworks often come into play.
Reference: apizee.com
Understanding Digital Assets
Digital assets represent discernible, owned items of value that companies store in digital formats. For instance, a document outlining a company’s processes holds intrinsic value, while a meme shared within a Slack channel does not. Here are examples of digital assets typically created and owned by companies:
Reference:
Knowledge Base Dedicated Page
Blog Dedicated Page
© 2024 Altos Web Solutions. All Rights Reserved!